What is Ransomware?
Ransomware Attack Types, Prevention And More
Jun 23, 2022Ransomware Definition
It is malicious malware that has the capacity of preventing the access of the user from their data. Then attackers demand ransom from the victim to restore access to the data upon the payment. The attackers instructed the victim about the payment method and in the end, got the decryption key to access their data. The range of the ransom depends on the attacker but mostly it is between a few hundred to thousands of dollars, and payable to the cybercriminal in crypto-currency.
What is Ransomware Attack – How it Works?
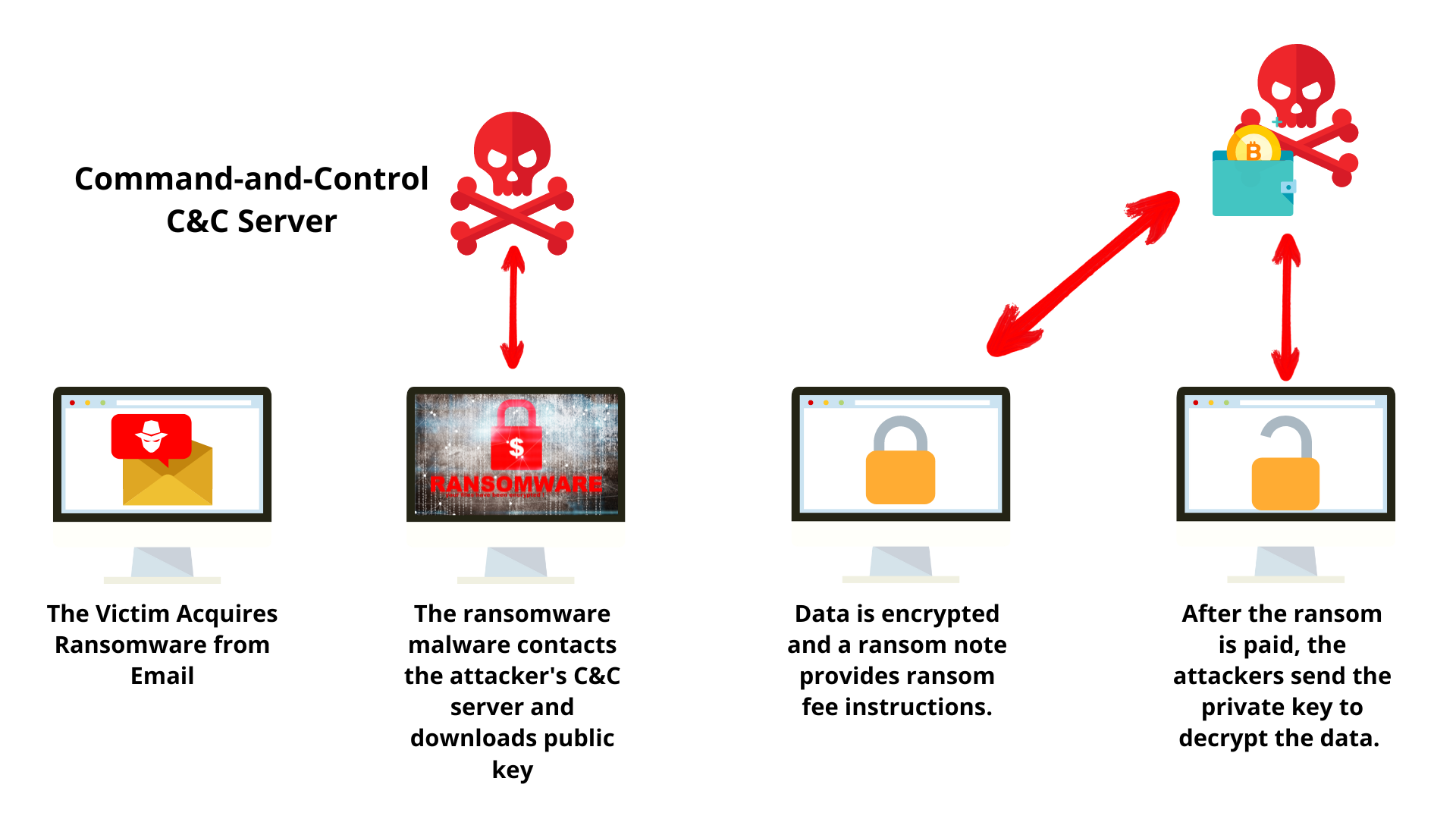
There are many ways ransomware enters the system and accesses the data and decrypts it. Here we will explain about the common ransomware attack as well as how it works and how it enters into the system. One of the common delivery systems of this malicious malware is phishing spam attachment that enters the user’s computer via email, pirated software, or any file from the internet. Attackers play with the mind of victims by using social engineering and manipulating the user into allowing the administrative or root access to the system. Some type of ransomware is not needed to trick the user; it exploits the vulnerabilities of the system and enters the system.
It is entered into the computer and encrypts the all-important data of the user, once the file is encrypted the attackers display a message through a web page or pop-up box. In the message, attackers tell the user how to pay the ransom, and ransomware has a one-week payment deadline, once the deadline is passed attackers may increase the ransom or the entire system is halted. Imagine this has happened with any firm: all their Client files are encrypted. The most important thing in this scenario is files are not decrypted without the mathematical key and the attacker has only that key. In most cases, user-pay all the ransom to the attacker because if the user lost the data that is a more irreparable loss. Here are a few ransomware attacks crippled parts of the country.
On the other hand, there is a positive use of ransomware in many countries, for example, law enforcement agencies shut down the victim’s computer due to the presence of pornography and other illegal software, and in-demand pay some “fine” to the government. However, the attacker targets a small firm because they do not have a well-established security system, that’s why they are easily manipulated by the attackers. Some large companies are targeted because they easily pay the ransom to the attack like the government or big accounting firms. The reason behind this is that data is very important for them. If the client sees their file is not secure they will not come to that firm in the future. But don’t feel you are safe if you are not using any anti malicious technique then you will be the next target.
Crypto Malware Attack – The Link Between Cryptocurrency & Ransomware
Crypto malware attack is a kind of malware that enables a threat actor to carry out cryptojacking movement. While the methodology used by hackers is the same as compared to that used by legitimate cryptominers, crypto malware leverages another user’s devices and processing power to attain payment.
Now let some talk about cryptocurrency here, it plays an essential role in the payment of the ransom to the attacker. A famous and most common use of cryptocurrency is bitcoins, it has no physical representation, they are stored in digital wallets and this currency is untraceable. We can buy anything through bitcoins all across the world, and transfer it from one place to another.
This is the ideal payment method for malicious persons because law enforcement agencies did not trace any place to transfer currency. After all, if the payment method is not safe then ransomware did not accomplish the attacker’s goals, with the help of cryptocurrency it’s like a dream come true. Most of the attackers are using the TOR (The Onion Router) browser development and enhancement of the anonymous attack. This browser is designed to hide the internet traffic that’s why we cannot find who sends that malicious malware.
Different Types of Ransomware:
Most of the Ransomware types such as wanna-cry and crypto-locker cripple many small and large businesses across the globe. Moreover, the first ransomware appeared in 1989, it used symmetric encryption. However, until 2012 there was an easy way to decrypt your device or computer after that with the arrival of the Reveton worm. This ransomware locks the computer of the user until the user pays the ransom. At the beginning of the 2014 crypto-ransomware technique was used by the attacker to encrypt all the data of the user if the user pays the ransom, the attacker gave a decryption key. There are three famous types of ransomware: the first is locker-ransomware, the second is crypto-ransomware and the last one is Mac Ransomware.
1. Locker Ransomware
Locker ransomware is the first type of ransomware that infects the PCs and locks all users’ files that are stored on the computers. It also accesses the whole computer’s data, this ransomware file is located on the PC until the user pays the ransom amount. Mostly this type of ransomware is used by Government officials if they see any prohibited material in the system. They lock the system (PC) of the user and ask for money as punishment. The working of this ransomware is very complex to understand, the AES encryption method is used to secure the passcode and it is almost impossible to guess the passcode. After the lock, all the files of the system, this malicious malware opens a window in which an attacker asks for a ransom. Does this window have total information about how to pay the ransom? And after paying the ransom how you will get the key to unlocking your system.
- Reveton:
Reveton is the only type of locker ransomware that has very less encryption use in it. The first appearance of this ransomware was at the end of 2012, it’s locking the user’s computer and shows the window in which they mention that the computer is locked by the FBI or the National Police. Now they ask for the money and remove all the prohibited data that is in the system. The message said your system has illegal content such as child pornography, pirated software, and content that is dangerous for the national security of any country. This ransomware almost hit 250,000 computer systems all over the world. If we see the working of the crypto locker they are very same as the working of this ransomware. Reveton attacked all the versions of the windows that are available in 2012 such as Windows XP, Windows Vista, Windows 7, Windows 8, and Windows 8.1. Apart from that Trojan downloaders produce this malware and install it as window services with a random file name.
2. Crypto-Ransomware
- CryptoLocker:
Crypto ransomware is the second type of ransomware as I mentioned above, this ransomware has many versions and types furthermore. The crypto locker is a type of crypto-ransomware. First, it was detected back in 2013 attacker change the technique of this ransomware. Because the previous version of ransom didn’t use any encryption method. It was the first example of the existing ransomware we were familiar with but of course many different versions.
This ransomware has a very advanced encryption method, it almost encrypts all the user data with a randomly generated symmetric key of every file. After that all the file was encrypted with over 70 types of encryption keys. The ransomware shows the message box which has mentioned everything like how to pay the ransom or how to decrypt the file by using the Asymmetric key. It also warns the user if he/she did any attempt with the Asymmetric key malware automatically removes all the data of the user. But we are very thankful the U.S State Department’s operation of justice disables the crypto locker in 2014.
- CryptoWall:
After the blocking of the crypto locker in 2014, attackers developed a new technique which we call the crypto wall. Then it has many different versions with a slight difference, with the name CryptorBit, CryptoDefense, CryptoWall 2.0, CryptoWall 3.0, and CryptoWall 4.0. One of the biggest features very important to note is that it is one single decryption key, the attacker gives you one file decryption that makes sure it is not a trap or fake.
When CryptoWall 4.0 is released in 2015 it has a very famous feature like malware encrypting the file name because the attacker didn’t want to tell the user which filename that is, if the user knows the file name they use the single decryption key to unlock that file that is more important for the user. Maybe after that the user didn’t pay any ransom to the attacker because the user’s major data is not encrypted. The ransom demand is starting from 700$ to 2000$ depending on the data sensitivity. When a system is infected, the OS of the system runs a different system connected to a different location and starts working with the command and control server that belongs to the attackers.
- Locky:
Locky was first detected in 2016, and most of the time it affected the system with Microsoft Office attachment files to emails. When the user opens the email and clicks on the office file it is directly downloaded into the system if the user opens it from the system on screen it opens the office file but on the back end, it allows the malware to run. After that when locky encrypted all the files of the user, the attacker set a note of ransom as a wallpaper which has many interactions such as web links to pay the ransom, and the date is also mentioned in that note. The latest version of this malware infected the user by using JavaScript, it automatically runs in the windows and they didn’t need any office attachments.
3. Mac Ransomware
- KeRanger:
This is the third type of ransomware family, KeRanger was developed in 2016 and it’s the first ransomware that successfully infected Mac OS X. In 2014 malware named FileCoder was detected on Mac OS but that ransomware was incomplete and didn’t work properly. KeRanger injected the installer of an open-source BitTorrent client that wanted to download the installer that infected all the computers. If the system is infected it waits for three days and encrypts 300 file types, and it automatically downloads the file of the payment method. The attackers give one key for free to the user to check if he can decrypt all the files if the user pays the ransom, otherwise, all the encrypted data will be deleted.
How Does Ransomware Work?
Ransomware is a type of malicious software, many attackers use this malware to infect the system for ransom. In this, there is the digital encryption that encrypts the system/computer files, the user didn’t access their files when they use the system. Now all in the hand of the attacker, they hold it until the user pays the ransom. After attackers infected one system they tried for another, one by one they attacked and conquered the whole network. If the ransom demands are not fulfilled cyber-criminal deletes all the data or publicizes the data over the internet. In some cases, the attacker encrypts the files with the 72 encryptions method and they only give one file key to the user to check that the attacker decrypts their data.
So the first thing is ransomware enters into the system in several ways, the most famous is downloading spam mail with attachment. When you open the attachment file in front of your screen there is some file like MS word but the backend software allows it to run ransomware. Another form of entry into the system is attackers using social engineering, downloading the ransomware in the system that attackers want to infect. More sophisticated versions of the ransomware are propagating themselves and can work without any human action.
So now we are discussing the brief introduction and working of the WannaCry ransomware, WannaCry is the type of crypto-ransomware. It also infects the system and encrypts the user’s file; they cannot read the file, WannaCry uses 92 encryption methods to encrypt the file. Mostly WannaCry ransomware attacks those systems which have MS windows because those computers are easily breached.
When the system is infected attackers ask for ransom and the ransom is only paid in the form of Bitcoins. In May 2017, WannaCry ransomware attacked the epidemic. The ransomware spread in the network through the computer that is using the MS windows in it. When the investigation was completed, the report said unskillful staff and lack of knowledge about the security of the network is the main reason behind such attacks.
The attackers are responsible for the attack, they took advantage of the MS windows weakness using a hack that was reportedly developed by the National Security Agency (USA). Microsoft released a security patch before the WannaCry ransomware but many large-scale windows have been used in different organizations. Unfortunately, most organizations didn’t update their security system, that’s why this ransomware exploits many organizations. The hack known as EternalBlue was developed by a group of people called shadow brokers before the WannaCry ransomware. Those that had not run a Microsoft Windows update before the attack did not benefit from the patch and the vulnerability exploited by EternalBlue left them open to attack.
Ransomware Attack Prevention:
There are several ways through which you can protect yourself from ransomware attacks.
- Do not open unknown email attachments
Ransomware can get into your computer through an email attachment. When one receives an email from an unknown person or the person whom he doesn’t trust, then one should not open the attachments associated with the email. Confirm the email address of the person who is sending that email. Make sure before that the attachment a person is going to open is original. If one has any doubts, contact the person and ask him to double-check the email. If the victim is not sure from whom the email is, then disregard it or don’t open the attachment. Even one should not open the attachment on Macros because if a person opens that attachment and it is affected, the malicious code will instantly run and take control of the victim’s computer.
- Only download from the websites which you trust
To minimize the risk of being infected by the malware do not download from unfamiliar websites. If you want to download go to verified websites that you know are trustable. Peek in the search bar to check if the websites use https rather than Http. A shield or lock symbol can also be shown in the search bar that is used to verify that the website is secure. The same thing applies to mobile phones also. Android users must download from the Google play store and IOS users from the App store.
- Do not use unfamiliar USBs
Do not insert USBs or other external storage devices into your device if you don’t know where they came from. Cyber Criminals may leave these kinds of devices in a public or on your private premises to attract you for using purposes.
- Do not give your details
If one ever receives a call, email, or text message from any untrusted or unidentified source and asks you to give your personal information, try to avoid that. Cybercriminals may try to use this information while trying to target you individually. Most of the time if they gain access to one’s details they may ask for ransom from their prey. It is strongly recommended that if one receives these kinds of requests, avoid them.
- Never open the unidentified links
When one happens to receive a spam email or any unknown links, do not try to open them, even links on unidentified websites. When one clicks on any of the links, downloading malicious code may start and that could get your computer infected. When ransomware is in the system, it will start automatically encrypting files or may lock the operating system. Once the system is locked or files are encrypted they may ask for ransom, paying that ransom may seem the easiest solution to decrypt your data, but this is the same thing attackers want you to do and there is no guarantee that you get your files back safely.
- Use mail servers’ proper filtering
Using the proper filtering and scanning on the mail server is one of the ways to prevent ransomware. The software used by different mail servers reduces the receiving of spam emails that may contain malware. These malicious files may also be deleted and will never show in the mailbox.
- Keep your operating system updated
Keeping your operating system up to date will help you protect yourself from malware. By doing so, the antivirus of the system will also be updated. The latest security patches make things harder for cybercriminals to exploit weaknesses in the software.
- Backup data periodically
The important data in the operating system must be backed up after some time. That data must be on different cloud and external drives. That external drive should not be connected to the infected system. In this way, if the data is even encrypted a victim can get back his original data from the backup. Cloud storages are the best solution for getting back your data.
- Pentest Your network and ongoing applications
Most important you must Pentest and vulnerability assessment of the network and if you have any application running on the specific network. Make the Cyber Security policy and implement it throughout the network.
Winding Up – Early detection helps prevention
Ransomware isn’t going anywhere – it seems like part of the new standard of cybersecurity. Ransomware attackers have ways to bypass cybersecurity measures, but you can shield your business. Always Keep Data Secure and Prevent Expensive Downtime. Cyber resilience needs cyber security solutions that can secure business continuity and prevent data loss or corruption.
Nuox Technologies provides end-to-end Cyber Security Services to every enterprise to prevent and mitigate any cyber hazards.